2 . System Architecture
The MetaSoilVerse Protocol (MSVP) is structured as a vertically integrated on-chain stack, enabling issuance, validation, leasing, and governance of Real-World Assets (RWAs). The architecture emphasizes modularity, verifiability, and on-chain enforcement of trust.
Each layer is logically and cryptoeconomically dependent on the other, forming a deterministic pipeline of value and validation. Below is a detailed breakdown of the six core layers.
2 .1 Asset Onboarding Layer
This is the entry point of any asset into the protocol.
Function : Accepts applications to onboard infrastructure assets (e.g., land parcels, solar farms, warehouses).
Inputs :
Proof of ownership or lease rights
Geographic and performance metadata
Initial jurisdictional metadata
Process :
Off-chain data is validated via notarized oracles, auditors, or asset operators
A one-time registration fee (in $MSVP) is submitted
Output : A unique asset hash is created, tied to metadata, and pushed into the Tokenization Layer.
Proof Mechanism: Proof of Origin & Control (PoOC) – Combines notarized claim + staking commitment from the registering address.
2 .2 Compliance & Identity Layer
To maintain jurisdictional flexibility, compliance is implemented as modular logic.
DID Registry : Asset operators and investors must create a decentralized identity (DID) bound to a jurisdictional compliance module.
zkKYC Support : Optional zero-knowledge proofs for validating age, nationality, or AML checks without revealing full identity.
Legal Plugin Architecture :
Composable modules for SPVs, trusts, or region-specific escrow logic
Regulatory hooks for real estate (REIT-like), energy, or mining domains
This layer ensures that RWA interaction on MSVP remains legally cognizant while still respecting the base layer ’ s permissionless ethos.
2 .3 Tokenization Layer
Once an asset is validated and jurisdictional compliance is bound, it is tokenized using ERC-721 or ERC-1155 standards.
NFTs represent unique ownership or lease claims
SFTs represent divisible access rights (e.g., per kWh for solar, per sqft for real estate)
Metadata is hosted on decentralized storage (IPFS or Arweave) and is hash-linked on-chain.
Token logic supports:
Time-based leasing
Revenue-share logic
Composability with DeFi protocols
The token ID is deterministically linked to the Asset Onboarding hash to prevent spoofing.
2 .4 Yield Vault Layer
Every asset token can optionally plug into a yield strategy.
Function : Route periodic returns (from real-world operations) back to token holders.
Architecture :
Vaults are configured per asset or asset class
Income is streamed in stablecoins or converted to $MSVP
Distribution Logic :
Follows pro-rata or time-weighted participation models
Includes slippage buffers and treasury rerouting
Mathematical Model : If Y(t) is the yield at time t , and H is the number of token-holders, the distributed yield per holder yᵢ(t) is:
This makes vault-based yield composable, predictable, and auditable.
2 .5 Staking & Delegation Layer
Staking is the backbone of protocol security and data integrity.
Who Stakes :
Asset operators (to ensure honest reporting)
Oracles (to prevent false feeds)
Validators (for network maintenance)
Delegation Model :
Token holders can delegate stake to operators and share in rewards
Slashing Conditions :
Downtime, tampered data, legal violations
Triggered via multisig or automated proof-of-misbehavior
This layer enforces economic skin-in-the-game for actors.
2 .6 Governance Mechanism
MSVP is governed by token-weighted (or optionally quadratic) DAO mechanics.
Proposal Lifecycle :
Submit → Review → Vote → Execute (via timelocked contracts)
Scope of Control :
Parameter changes (fees, caps, staking durations)
New asset categories or compliance modules
Treasury allocation and emissions
Stakers and long-term participants can accumulate governance weight, allowing protocol evolution without compromising decentralization.
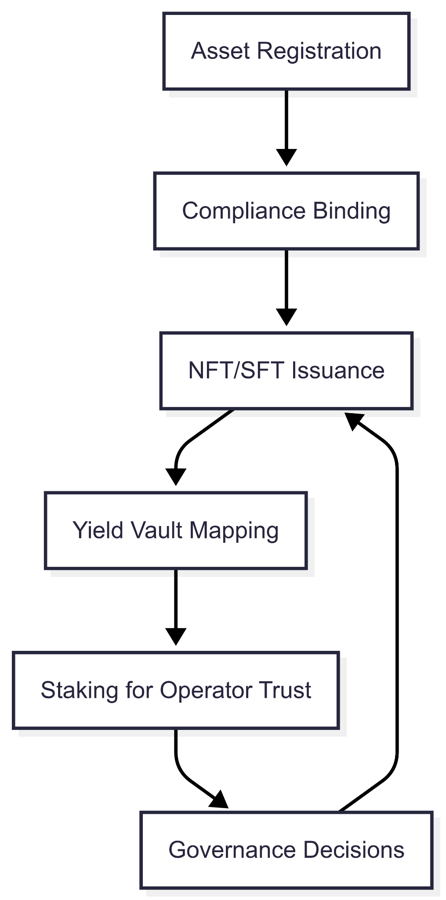
2 .7 Logical Flow Across Layers
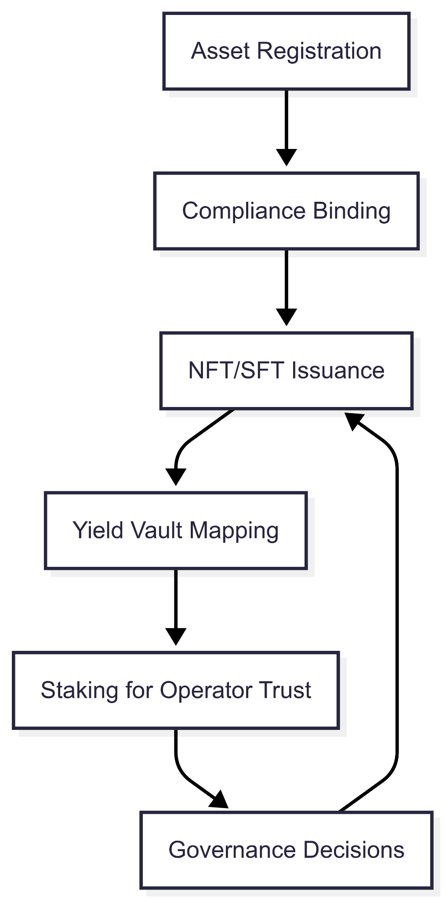
Each layer feeds the next with authenticated, verifiable data and commitments , ensuring a system where value cannot exist without validation, and validation cannot be spoofed without risk.